Featured
Table of Contents
How To Choose A Vpn — 9 Things To Consider When ...
Another factor to consider in picking a VPN is how strong the file encryption is. More powerful encryption is more difficult to break and offers better security. 256-bit encryption is basic in the VPN industry, although some suppliers provide less-secure 128-bit encryption. Inspect the service provider's website under the "features" section, and they need to market what level of file encryption they utilize.
To see the number of are on deal, look for a section on the provider's website entitled "Server List" or similar - what are some factors to consider when choosing a vpn provider. This need to reveal you a total list of all the servers that are readily available and their areas. Generally speaking, more servers is much better as it provides you more options to find a fast and reliable server when you link.
Simply look for a company with a minimum of 500 servers which should be sufficient for the majority of people. You will also want to check the number of countries servers are offered in. You can use a VPN to get around local limitations as long as your company has a server in the nation you wish to access the web from.
The Best Vpn Software To Keep Your Data Secure
One downside to using a VPN is that it can decrease your web connection a little due to the extra encryption step that the data goes through. To lessen this slowdown, you'll desire a VPN that has fast servers. It can be tough to find out how quickly a VPN will be.
You can search for VPN reviews which typically consist of a speed test, however keep in mind that your experience will be different from somebody else's. This is since the speed of your connection will depend upon both where you lie and where the server that you are connecting to is located.


Many VPN service providers use a free trial or a money-back warranty to try their servers for a few days and see if you are pleased with the speeds prior to devoting to one company. Prior to you decide, you can also examine what optional features a VPN supplier uses by inspecting their website.
What Is A Vpn And What Does It Do?
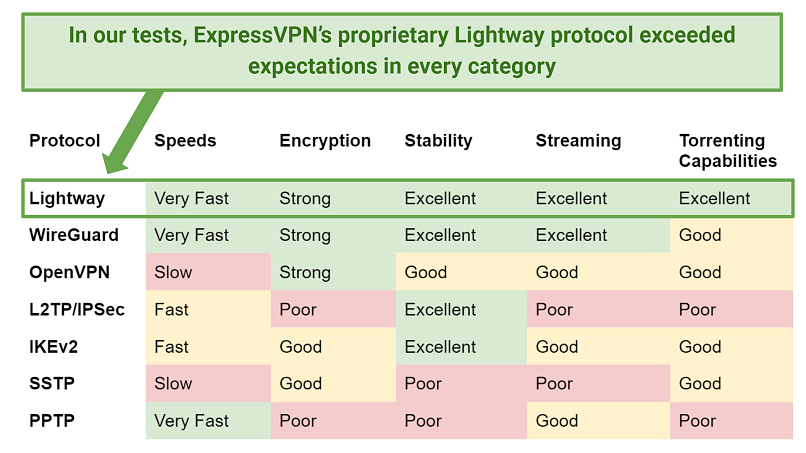
They are the core technology that determines how your information is routed to the VPN server. There are a variety of significant VPN protocols, and they are not produced equal.

Put in the time to discover the ideal VPN for youstart with our guide to the very best VPN services. If you're uncertain where to begin, we recommend Express, VPN or Personal Internet Access. Follow our links and conserve on a membership!.
At minimum, we can assume all users have the same IP address (due to being connected to the very same server) and therefore have the same "exit node." This makes it harder for the numerous websites, web services, or web apps to select who is who, even if multiple users go to the same site at various times (what are some factors to consider when choosing a vpn provider).
Vpn Management Best Practices For All Situations
In many cases, totally free VPN suppliers have shared information with cloud service providers, federal governments, and anybody going to supply some money in exchange for the information; they have likewise been accused of using device resources, such as CPU power, to mine crypto for themselves (cryptojacking)! Among the most crucial things to look for in a VPN supplier is the contents of their data personal privacy - specifically information collection and any possible retention of collected data - policies.
If the VPN provider collected PII, then these logs could be utilized and tied back to a user's true identity. For that reason, efforts of openness can prove essential to keep in mind. It's frequently worth digging much deeper than what the marketing claims (or conveniently overlooks) on the VPN supplier's site, considering questions such as: Does the VPN supplier offer a publicly available audit of their no-logs claims? Exist openness reports that reveal demands gotten by government entities? What was the date of the last audit? Is an audit on a VPN provider's no-logs policy conducted frequently? Does the VPN company share information - such as logs - with 3rd parties (which can include server facilities companies and government entities.) Details needed at signup Ask for individual identifiable details (PII) may be spun to appear harmless - a thanks to the VPN's marketing department.
To reduce this, trusted VPN providers typically provide alternative types of payment - and even anonymous payments. Alternative types of payments, such as accepting Bitcoin or Litecoin, aren't always anonymous; typically anonymous payments consist of accepting Monero cryptocurrency and money. Depending on the user, this may not be a location of great issue.
Secure Your Online Privacy: How To Choose The Best Vpn ...
With open-source clients, anyone can check the source code for any factor. Open-source clients normally also show a dedication to contributing to the open-source community too. Tweaks/adjustments can be more quickly done or recommended by users happy to do so. If the VPN company's customers are not open-source, then it's encouraged to For instance, does the VPN customer app collect any gadget information? Does the customer have embedded trackers? Consents such as bluetooth and location services access should be related to with suspicion as they are not required to render VPN services.
Procedures Protocols are the engine behind VPN connections. Typically, centralized VPN providers use multiple procedures; the user often chooses which protocol to use. A couple of different VPN protocols exist and there is no "best" option; VPN companies need to provide at least User requirements and requirements usually dictate which protocol to pick over the others (what are some factors to consider when choosing a vpn provider).
Latest Posts
The Top 10 Enterprise Vpn Solutions
Advantages And Disadvantages Of A Vpn
10 Best Cloud Vpn Providers In 2023